The prosperity of internet development has changed our daily lives. The internet has created convenience and shortened the urban-rural gap; however, cyber security risks have also arisen, such as internet scams, personal data leakage, ransomware, and computer viruses; these incidents have been on the rise. Corporations should especially focus on cyber security. Cyber security incidents not only result in financial loss but also negatively impact a corporation’s reputation and credibility.
TDCC’s cyber security protection has always been in the lead. The cyber security protection is conducted collectively through three lines of defense: defensive exercises, gateway tire protection, and endpoint protection so that each kind of attack can be fended off to achieve the goal of risk aversion. Each line of defense achieves joint defense through various security mechanisms and tools. The most significant risk in endpoint defense is from the internet. When layers of defense mechanisms fail to detect malware and zero-day attacks, series of cyber security disasters may arise. Nowadays, these threats usually happen when surfing the internet. Even famous and official websites may be injected with malware (also called “watering hole”). Without being noticed, unsafe documents or malware may be downloaded or executed carelessly. In addition, users may mistakenly click on a malicious link or phishing site (social engineering), and activate a malicious program or other attacks through enticement. This may lead to infection of the computer or lock and encrypt the files on your computer.
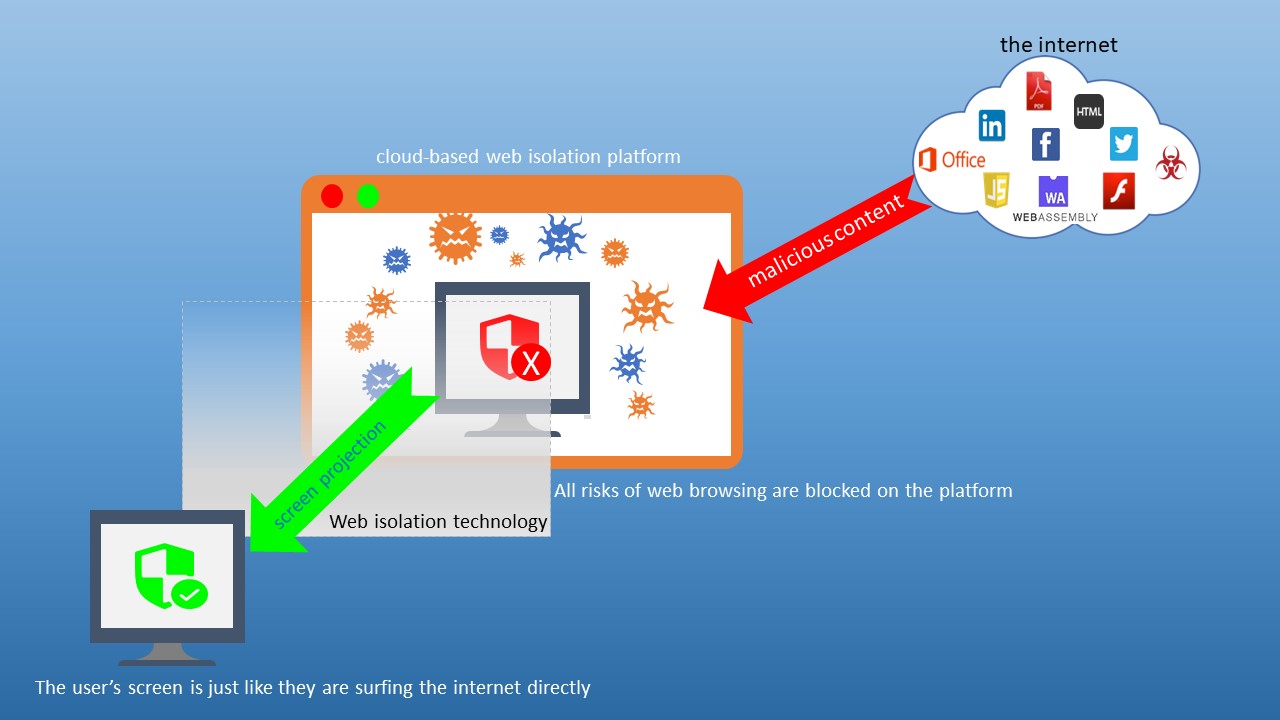
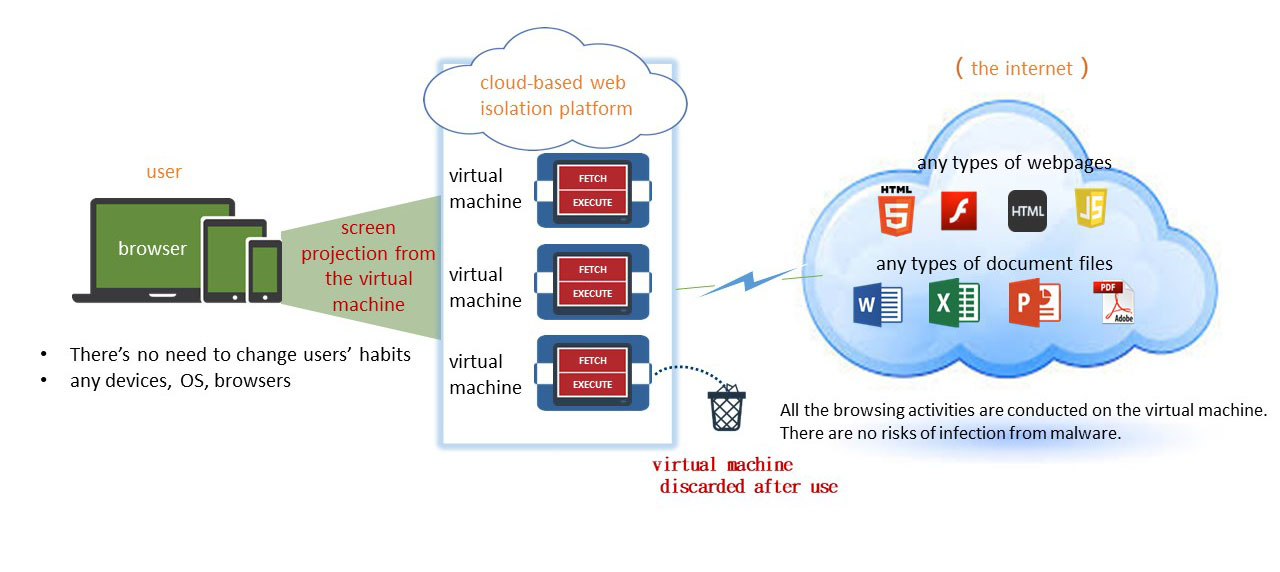
Web isolation is a mechanism to prevent the threats mentioned above. It can reduce risks as employees go online, and prevent files with viruses and malicious programs from being downloaded from malicious websites. As employees go online, the web isolation platform provides protection automatically, the platform is like a glass box, isolating risks and keeping them out. The behavior of users browsing the internet is executed on the cloud-based web isolation platform. It isolates browsing activity away from end user's devices and onto remote cloud servers that they operate. The server is completely separated from the user's endpoint and business networks, which fully protect users from any threats in a browsing session. In other words, even if users browse a malicious website, the malicious content will not be executed on the user side. As a result, the user's device will not suffer from malicious threats and infections, and the user's device will not be infected.
When introducing cyber security tools, there is usually a trade-off between security and efficiency, and it often changes the original operating habits of users, which brings users’ complaints and decreases users’ system satisfaction. However, the introduction of the cloud-based web isolation platform does not change users' original internet habits.
Although users’ web browsing is executed on the isolation platform, it may still cause potential risks to the enterprise when users download files to their devices. Before a file is downloaded, the cloud-based web isolation platform will conduct file attribute code comparison, anti-virus detection, and sandbox verification.
Files can be classified as document files and non-document ones (such as executable files or compressed files). Most of the document files are only for users’ references, so there’s no need for editing. On the cloud-based web isolation platform, document files can be transferred into PDF format for previews in web browser or downloads to users’ computer. The rendered content is consistent with the original file. This not only provides users with a preview, but also ensures safe browsing of the file.
If the document file still needs editing after previews, the cloud-based web isolation platform also provides the download function for the original file, and the protection for download is the same as that for non-document files. On the cloud-based web isolation platform, the file will go through procedures such as file attribute code comparison, anti-virus detection, and sandbox verification. Only if the content is confirmed harmless will the file be allowed for downloads. This can effectively minimize risks from the internet.
Even though the cloud-based web isolation platform can effectively reduce the risks from the internet, the threats to cyber security are not from the internet only. On a regular basis, user account authorization should be inspected, operating system and software should be patched and updated, and related cyber security tools (such as anti-virus software) should be installed in computers on each endpoint. Special caution should be given to the use of email. Emails, links and attachments in emails from unknown users or for non-official purposes shouldn’t be clicked on to prevent email social engineering attacks.
To sum up, the two key features of web isolation are as follows:
1. Surfing the internet is performed on the web isolation platform. The user's browser screen is only the screen projected on the cloud-base web isolation platform. This is like the idea of “watching the fire from the opposite bank of the river”. All the risks are blocked on the web isolation platform.
2. Checking before downloading files from the internet.The platform will conduct file attribute code comparison, anti-virus detection, and sandbox verification to ensure the file doesn’t contain any malware.
To conclude, security mechanisms and tools can help to minimize risk of cyber security; however, security awareness is also important. TDCC have been not only adopting security mechanisms but also undergoing security awareness training periodically to guarantee its business operation and safely.